Splunk count number of events – Embark on a journey into the world of Splunk event counting, where data becomes your ally and insights emerge from the digital depths. Dive into this comprehensive guide to unlock the power of Splunk and harness the true potential of your event data.
In this exploration, we’ll uncover the secrets of counting events like a pro, unravel the mysteries of custom dashboards, and delve into the art of optimizing event counting performance. So, buckle up and get ready to elevate your Splunk skills to new heights.
Overview of Splunk’s Event Counting Functionality
Splunk’s event counting feature enables users to quantify the occurrence of specific events within their data. This capability is essential for various use cases, such as monitoring system activity, tracking user behavior, and detecting anomalies.
By leveraging Splunk’s event counting functionality, organizations can gain valuable insights into their data. This information can help them identify trends, optimize processes, and make informed decisions.
Benefits of Using Splunk to Count Events
- Real-time monitoring:Splunk provides real-time visibility into event counts, allowing users to monitor system activity and user behavior in real time.
- Historical analysis:Splunk stores historical data, enabling users to analyze event counts over time and identify trends and patterns.
- Customization:Splunk allows users to customize their event counting queries to focus on specific events or time periods, providing flexibility and adaptability.
- Integration with other tools:Splunk can integrate with other tools, such as SIEMs and ticketing systems, to automate event counting and incident response.
Methods for Counting Events in Splunk
Splunk provides various methods to count events, enabling you to analyze and extract meaningful insights from your data. This section delves into the techniques for event counting, empowering you to efficiently quantify and track events of interest.
Using the Search Command
The search command is the primary tool for counting events in Splunk. By specifying search criteria, you can filter and count events based on specific conditions. Here’s a step-by-step guide:
- Enter the search command:
search - Specify the search criteria: Use field extractions, operators, and logical expressions to narrow down the events you want to count.
- Count the events: Append the
| stats countcommand to count the matching events.
Example:
search sourcetype=web_logs | stats count
Wildcards and Modifiers for Flexible Counting
Splunk offers wildcards and modifiers to enhance the flexibility of event counting. Wildcards, such as *and ?, allow you to match multiple characters or single characters, respectively. Modifiers, like mvcount, provide additional counting options.
Example:
search sourcetype=web_logs error_code=*4* | stats count mvcount(error_code)
Advanced Event Counting with Stats, Splunk count number of events
The stats command provides advanced capabilities for event counting. It allows you to perform various statistical operations, including:
- Sum:
stats sum(field) - Average:
stats avg(field) - Minimum:
stats min(field) - Maximum:
stats max(field)
Example:
search sourcetype=web_logs | stats avg(response_time)
Customizing Event Counting in Splunk
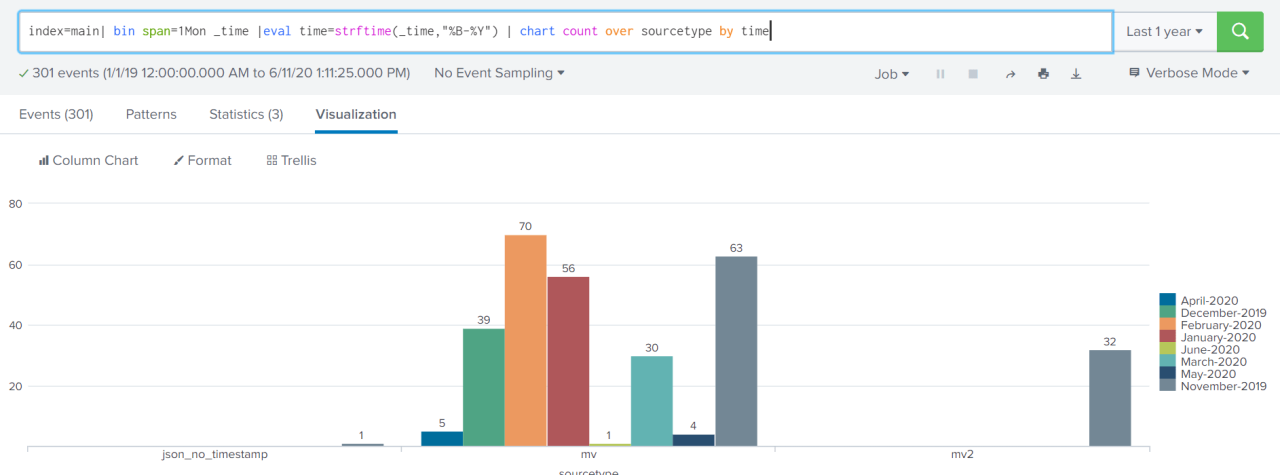
Customizing event counting in Splunk allows for tailored dashboards, alerts, and reports to meet specific monitoring and analysis requirements.
Custom Event Counting Dashboards
Create custom dashboards to visualize event counts over time, by category, or any other relevant metric. Dashboards provide an intuitive interface for monitoring key performance indicators (KPIs) and identifying trends or anomalies.
Counting the number of events in Splunk can be a breeze, but if you’re looking for a delightful distraction, why not take a break and check out young ferns 7 little words ? It’s a fun word puzzle that will keep your mind sharp.
When you’re ready to get back to counting events, Splunk will be waiting for you.
Alerts and Reports for Event Counting
Configure alerts to trigger notifications when event counts exceed predefined thresholds. This enables proactive monitoring and timely response to potential issues. Generate reports to summarize event counts, identify patterns, and provide insights for decision-making.
Real-World Use Cases for Customized Event Counting
- Monitor website traffic and identify spikes in activity to optimize server performance.
- Track security events and generate alerts for suspicious activity to enhance cybersecurity.
- Analyze customer behavior and identify patterns in product usage to improve user experience.
Best Practices for Event Counting in Splunk: Splunk Count Number Of Events
Event counting in Splunk is a crucial aspect of data analysis, but it comes with its own set of challenges. To ensure accuracy, reliability, and optimal performance, it’s essential to follow best practices.
Common Pitfalls and Challenges in Event Counting
Some common pitfalls to avoid include:
- Overlapping time ranges: Overlapping time ranges can lead to double-counting of events.
- Incomplete data: Missing or incomplete data can result in inaccurate event counts.
- Ambiguous event definitions: Unclear event definitions can lead to inconsistent counting.
- Performance issues: Complex event counting queries can slow down Splunk performance.
Optimizing Event Counting Performance
To optimize event counting performance, consider the following:
- Use summary indexes: Summary indexes can significantly improve performance for large datasets.
- Optimize queries: Use efficient search commands and avoid unnecessary calculations.
- Leverage time-based indexing: Time-based indexing can enhance performance for time-series data.
Ensuring Accuracy and Reliability of Event Counts
To ensure accuracy and reliability, follow these tips:
- Validate data: Check the quality and completeness of the data before counting events.
- Use consistent event definitions: Define events clearly and consistently to avoid ambiguity.
- Test and verify queries: Test and verify event counting queries to ensure they return accurate results.
Essential Questionnaire
Q: How do I count events using Splunk’s search command?
A: Utilize the search command along with appropriate filters and modifiers to retrieve and count specific events.
Q: What are some best practices for optimizing event counting performance?
A: Employ techniques such as indexing, filtering, and leveraging summary statistics to enhance the efficiency of your event counting queries.
Q: How can I create custom event counting dashboards in Splunk?
A: Utilize Splunk’s dashboarding capabilities to visualize and monitor event counts in real-time, enabling you to gain instant insights into your data.